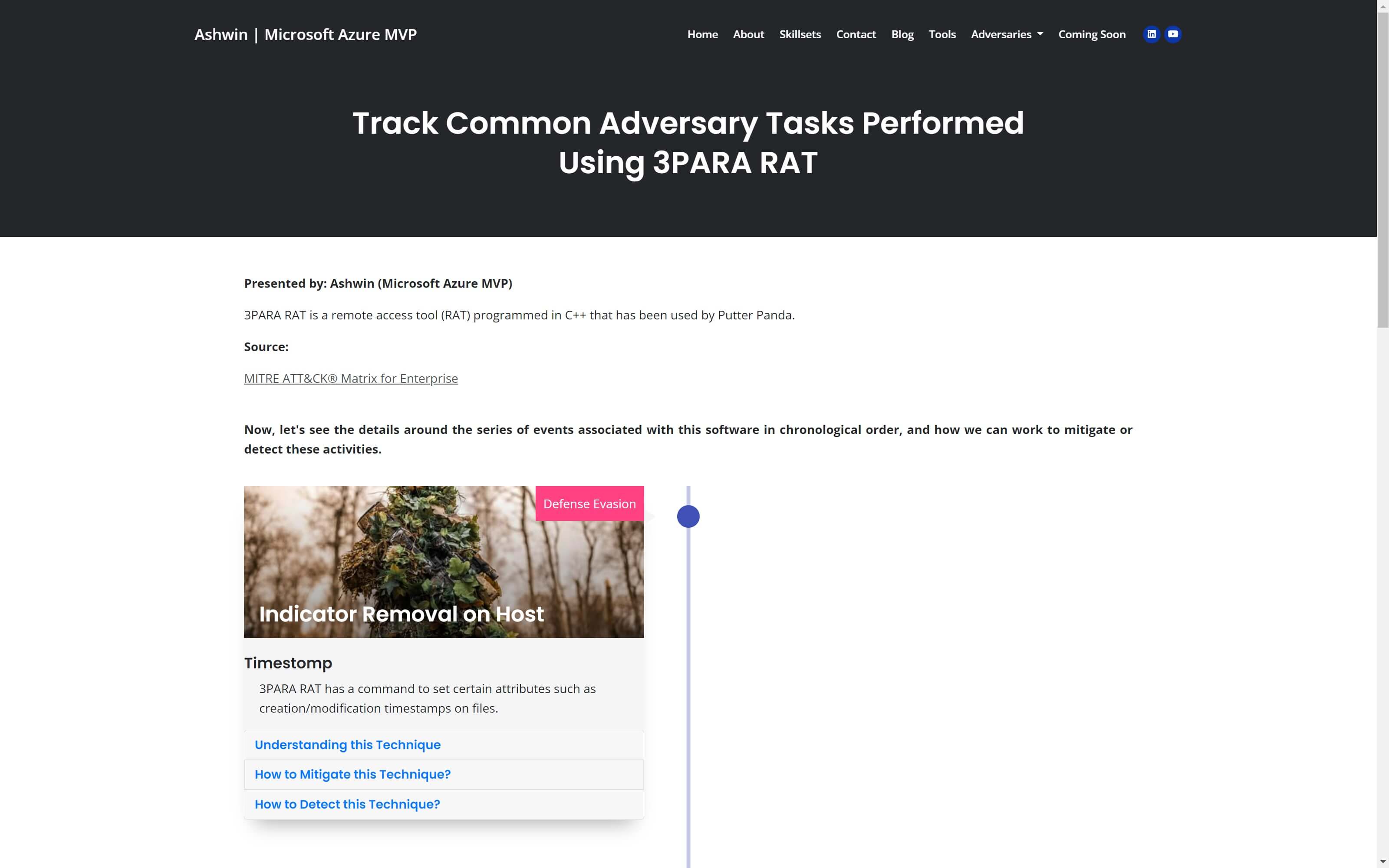
Track Common Adversary Tasks Performed Using Cobalt Strike
Presented by: Ashwin (Microsoft Azure MVP)
Cobalt Strike is a commercial, full-featured, remote access tool that bills itself as "adversary simulation software designed to execute targeted attacks and emulate the post-exploitation actions of advanced threat actors". Cobalt Strike’s interactive post-exploit capabilities cover the full range of ATT&CK tactics, all executed within a single, integrated system.
In addition to its own capabilities, Cobalt Strike leverages the capabilities of other well-known tools such as Metasploit and Mimikatz.
Source:
MITRE ATT&CK® Matrix for Enterprise
Now, let's see the details around the series of events associated with this software in chronological order, and how we can work to mitigate or detect these threats.
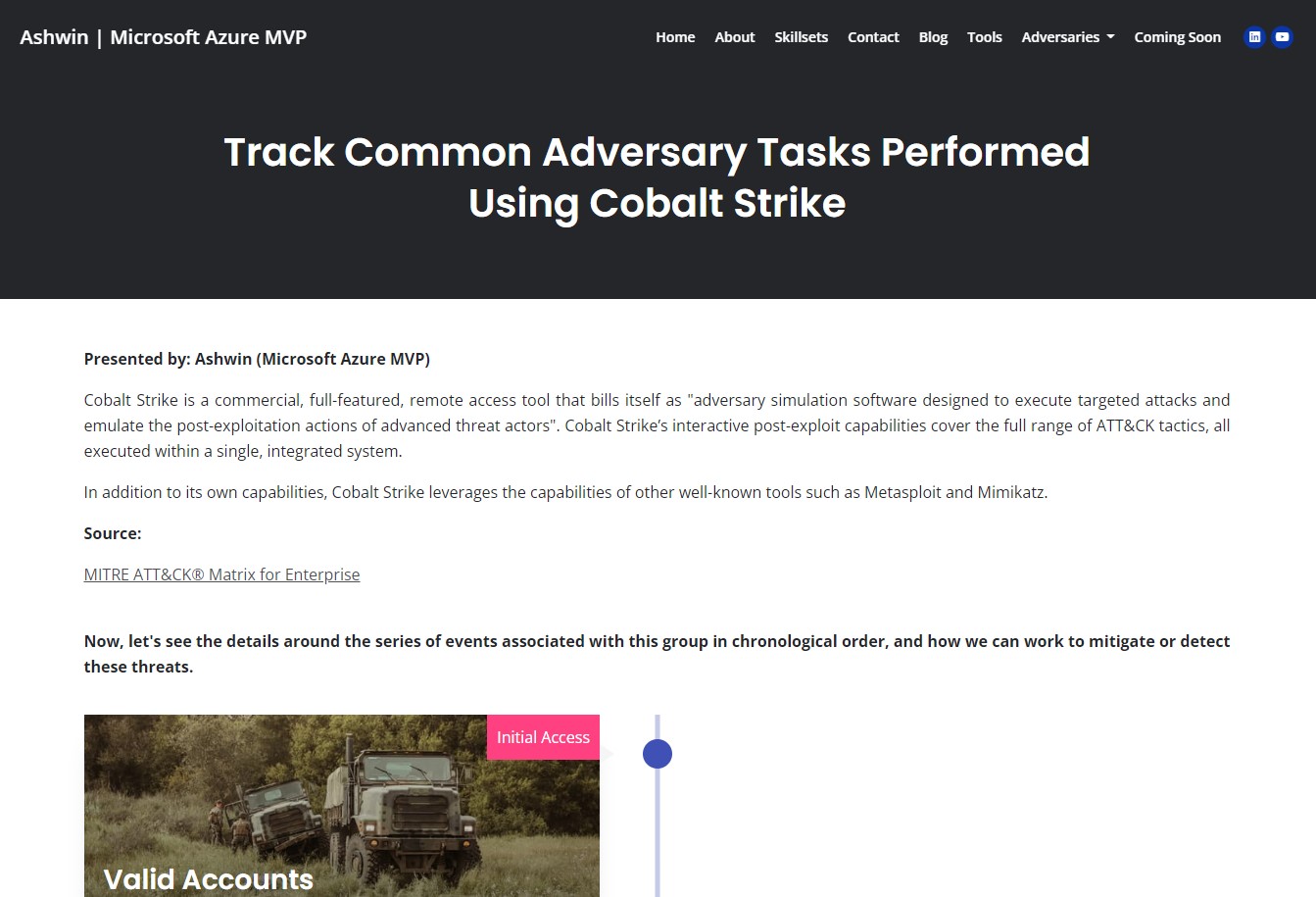
Track Common Adversary Tasks Performed Using Mimikatz
Presented by: Ashwin (Microsoft Azure MVP)
Mimikatz is a credential dumper capable of obtaining plaintext Windows account logins and passwords, along with many other features that make it useful for testing the security of networks.
Source:
MITRE ATT&CK® Matrix for Enterprise
Now, let's see the details around the series of events associated with this software in chronological order, and how we can work to mitigate or detect these activities.
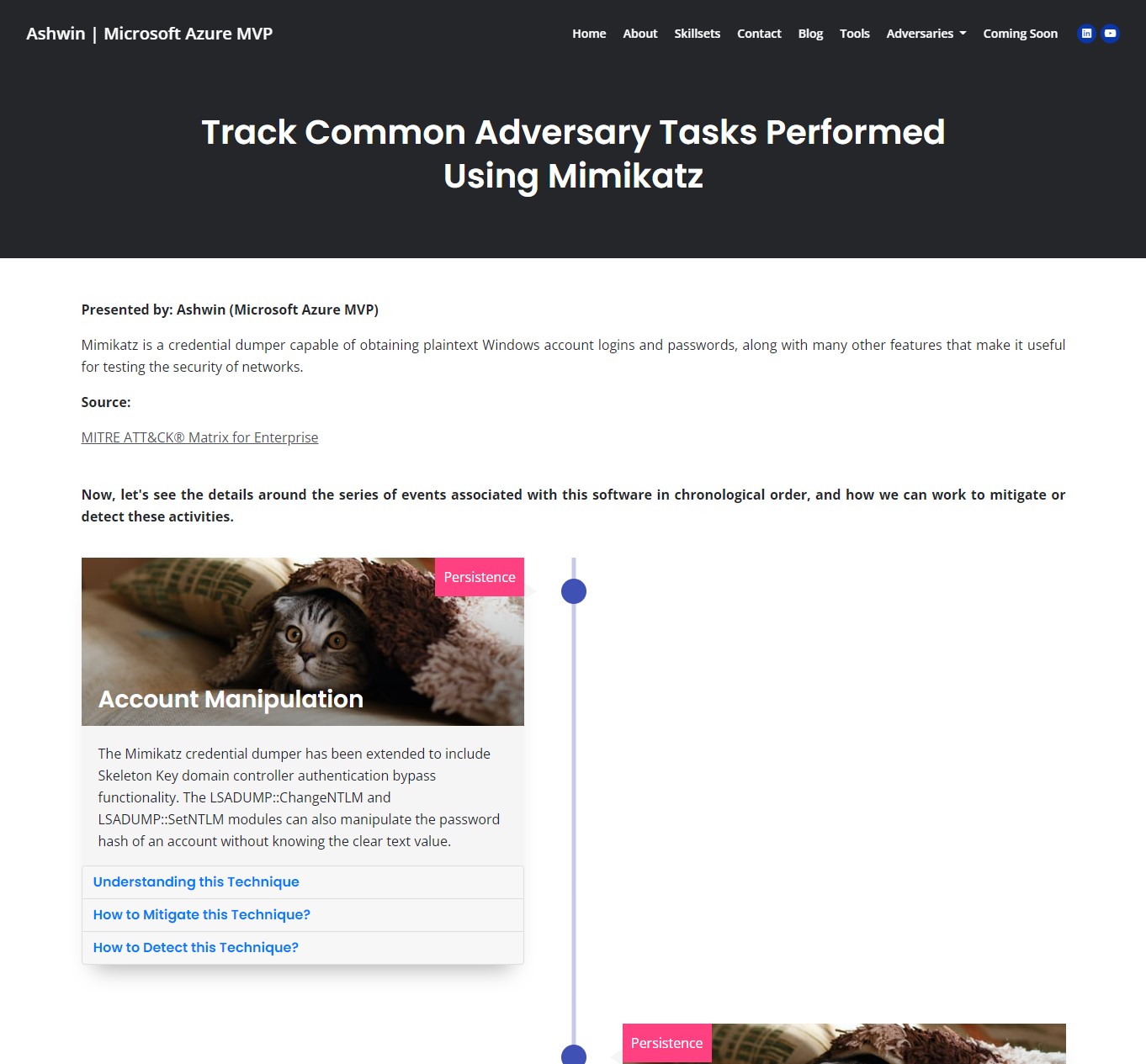
Track Common Adversary Tasks Performed Using PsExec
Presented by: Ashwin (Microsoft Azure MVP)
PsExec is a free Microsoft tool that can be used to execute a program on another computer. It is used by IT administrators and attackers.
Source:
MITRE ATT&CK® Matrix for Enterprise
Now, let's see the details around the series of events associated with this software in chronological order, and how we can work to mitigate or detect these activites.
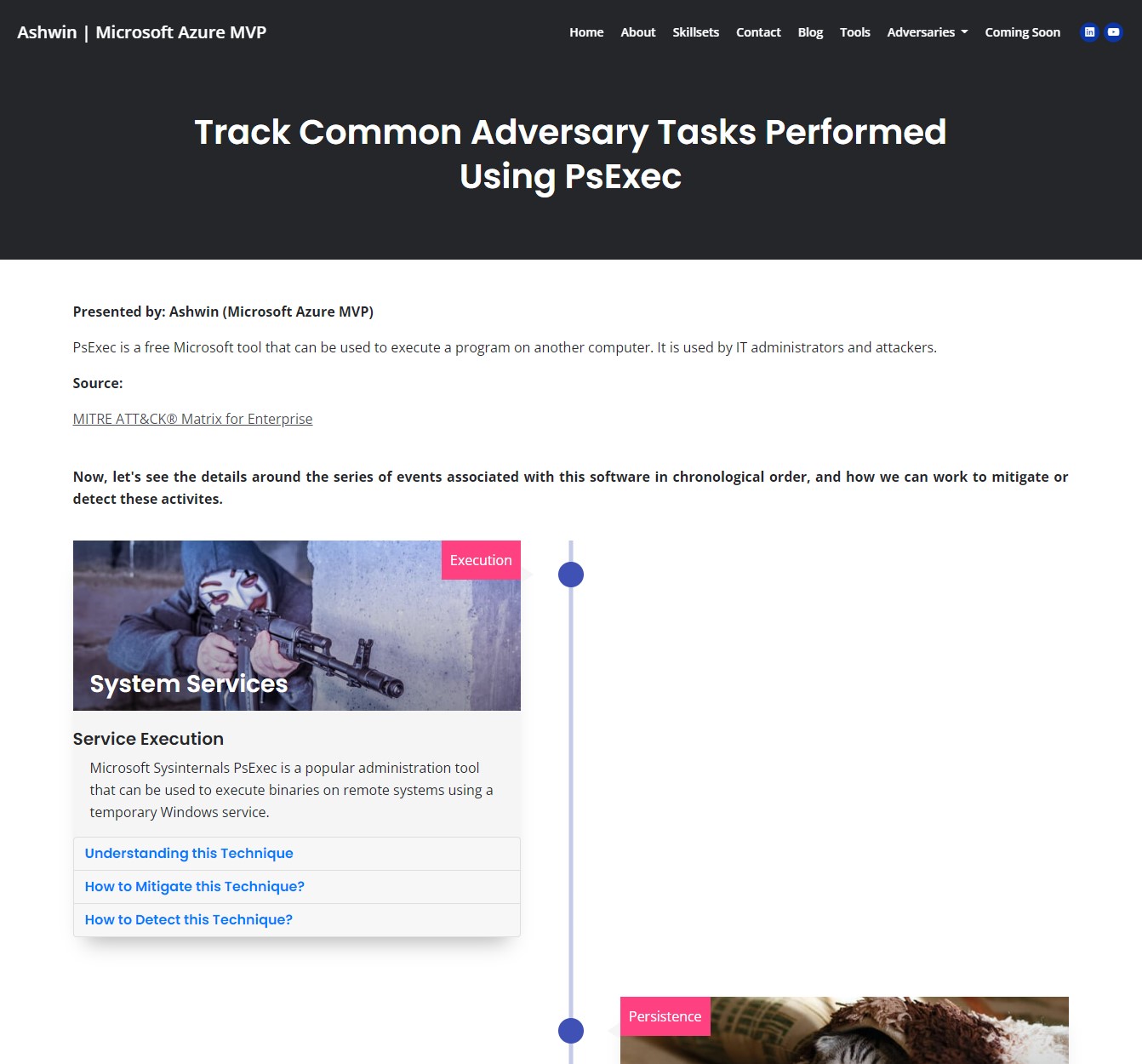
Track Common Adversary Tasks Performed Using 3PARA RAT
Presented by: Ashwin (Microsoft Azure MVP)
3PARA RAT is a remote access tool (RAT) programmed in C++ that has been used by Putter Panda.
Source:
MITRE ATT&CK® Matrix for Enterprise
Now, let's see the details around the series of events associated with this software in chronological order, and how we can work to mitigate or detect these activites.